Welcome to DJ's Junk Drawer.
Tuesday, May 31, 2011
What Your College Major Is Worth [Education]
Deciding what to major in or whether to get a graduate degree? This new report from Georgetown University may help. The report demonstrates the strong link between college majors and lifetime earnings, and also shows the earnings boost for graduate degrees by major. More »
Linus Torvalds approves Linux 3.0 RC1
 Linus Torvalds, the man who initiated the development of Linux, is still the chief architect of the Linux kernel and acts as the project's coordinator. Yesterday, he approved the first release candidate for the next version of the Linux kernel: Linux 3.0. You can see the commitdiff yourself on Git,...
Linus Torvalds, the man who initiated the development of Linux, is still the chief architect of the Linux kernel and acts as the project's coordinator. Yesterday, he approved the first release candidate for the next version of the Linux kernel: Linux 3.0. You can see the commitdiff yourself on Git,...

Monday, May 30, 2011
NVIDIA's Kal-El Glowball Shows off Dynamic Lighting & Quad-Core Physics on a Tablet
I've warned both Qualcomm and TI that the danger they have to face in the SoC space going forward isn't just NVIDIA engineering, but NVIDIA marketing. Although too aggressive for my tastes at times, NVIDIA does know how to take a simple product release and turn it into an extremely polished technology launch. Even down to the materials NVIDIA shares with the press, to-date none of its competitors have built such pretty slides that make their way all over the web.
Obviously it's not just marketing with NVIDIA. After a rough start the Tegra 2 finally got real traction and has been the premier Android smartphone and tablet SoC since the beginning of the year. If you're buying an Android smartphone or tablet today, chances are the best option uses Tegra 2.
At MWC earlier this year NVIDIA announced its third applications processor, codenamed Kal-El. Kal-El will feature four ARM Cortex A9 cores with a shared 1MB L2 cache and MPE/NEON support (absent from Tegra 2). Kal-El will also fix the video decoder issue we've run into on Tegra 2 and should be able to play all high profile H.264 content with proper OS support. On top of all of that there's a faster GPU (12-core vs. 8-core plus higher throughput per core).

What does all of this have to do with NVIDIA's marketing? Today NVIDIA posted one of its famous tech demos running on a Kal-El reference platform to show off what's possible with the new SoC. Read on to check out the video.
NVIDIA GeForce GTX 560M: High-End Mobile Graphics with Optimus
Our collective wishes have been granted by the fine folks at NVIDIA: you can now buy a notebook with high-end graphics that supports Optimus and thus is capable of offering excellent battery life. NVIDIA is refreshing their GeForce GTX 460M with the 560M. This will be a faster GPU, naturally, using the updated GF116 instead of the 460M's older GF106.

The impending ASUS G74Sx will be powered by the GeForce GTX 560M.
Notebooks using the new chip should be available in the near future, though keep in mind that not all notebooks will support all features. Read on for more details.
Sunday, May 29, 2011
Dept. of Defense and Homeland Security confirm Lockheed Martin hacker breach

Reuters has a followup to their scoop yesterday about an unspecified hacker attack involving Lockheed Martin, the world's biggest aerospace firm and the top US military supplier by sales: the DoD and the DHS are now involved, and confirm that a breach took place.
As reported yesterday, the Lockheed intrusion may be linked to the RSA SecurID breach disclosed two months ago. Reuters reports today:
The Department of Homeland Security said it and the Defense Department had offered to help gauge the scope of a 'cyber incident impacting LMCO,' as the maker of fighter jets, ships and other major weapons systems is known. The U.S. government also has offered to help analyze 'available data in order to provide recommendations to mitigate further risk,' Chris Ortman, a Homeland Security official, said in an e-mailed reply to a query from Reuters.
It was not immediately clear what kind of data, if any, was stolen by the hackers. But military contractors' networks contain sensitive data on arms that are under development as well as technology used by U.S. forces in Iraq and Afghanistan.
No word yet on whether other military contractors that also use RSA's SecurID system have experienced similar problems.
Thursday, May 26, 2011
What would a teaspoonful of neutron star do to you? [Ask A Physicist]
In this week's 'Ask a Physicist' we're going to consider an incredibly ill-conceived mission: a trip to a neutron star to extract the gooey neutrons inside. What happens next? You die. We'll find out how. More »
What Five Days of Deadly Tornadoes Looked Like From Space [Video]
It's hard to believe that this beauty can cause so much grief and damage, but from space even the deadliest of natural disasters always looks strangely soothing and mesmerizing. Those explosions of clouds seem to come from Earth herself. More »
Wednesday, May 25, 2011
DIY efforts to prevent Mississippi River flood damage

Popular Science has a photo gallery of houses surrounded by DIY levees, making them look like tiny islands.
This is the most important star in the universe [Space Porn]
This star may not look like much, but in 1923 it changed our understanding of the universe forever. It showed us that the Milky Way wasn't a lonely island universe, but instead just one of billions and billions of galaxies. More »
Tuesday, May 24, 2011
50 years of NASA art at National Air and Space Museum in DC, opening May 28

Above, 'Sunrise Suit-up,' Martin Hoffman, 1988, mixed media: 'Television screens in the media area at the Kennedy Space Center. The launch pad can be seen in the distance beyond Banana River. It is one moment of calm before the frenzy of launch activity.'
This work is on display at the National Air and Space Museum's Mall building from May 28 to Oct. 9, 2011, as part of the 'NASA | Art: 50 Years of Exploration' exhibition.
Tool reveals ISP traffic-shaping
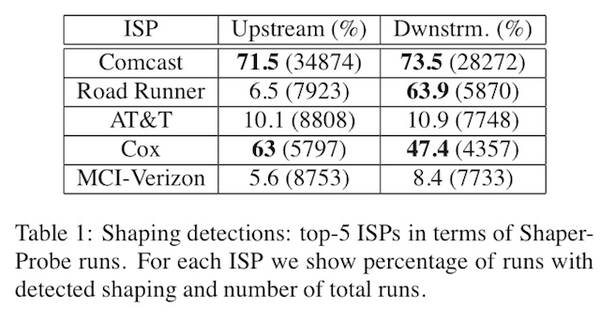
ShaperProbe is a research tool from a team at Georgia Tech that detects and characterizes 'traffic shaping' by ISPs, determining which US ISPs deliberately slow down their customers' traffic, and in what way they do so. They've published a paper on their findings, which indicate that cable ISPs do much more 'shaping' than telcos, with Comcast and Cox being the most aggressive, even slowing down the traffic you send, in addition to the traffic you receive. Georgia Tech researchers recently demonstrated another tool, Kermit, which also measures ISP performance. Both projects were funded by grants from Google, who have a clear interest in helping Internet users determine which ISPs practice throttling and shaping (notwithstanding Google's Net Neutrality sellout with Verizon).
The use of shapers can also be dictated by the underlaying access tech. The researchers note that DSL providers can 'dynamically change link capacity instead of shaping, while a cable provider is more likely to shape since DOCSIS provides fixed access capabilities.' It can also be applied to the entire Internet link or more narrowly to specific kinds of traffic-- which, as the researchers note, is 'relevant to the 'heated' network neutrality debate.'
The research shows that Comcast, Road Runner (from Time Warner Cable), and Cox all use downstream shaping--but only Comcast and Cox also use upstream shaping. Neither AT&T nor Verizon shape in either direction.
New 'ShaperProbe' tool detects ISP traffic shaping
End-to-end Detection of ISP Traffic Shaping using Active
and Passive Methods
Cops Scramble Helicopters and Tranquilizer Teams to Take Down Stuffed Tiger [Wtf]
GOOD GOD MAN, RUN. RUN QUICKLY! SAVE YOURSELVES, THERE'S A VICIOUS BEAST PROWLING. CALL THE POLICE! CALL THE ZOO! CALL—Wait, what? What'd you say? It's just a stupid stuffed animal? Aw crap. More »
Monday, May 23, 2011
Joplin, MO

At least 116 people have died in Joplin, Missouri, and the toll is expected to climb. One of the deadliest tornadoes in state history roared through the small Midwestern city on Sunday, leaving a half mile-wide scar and unbelievable destruction.
Touching down at about 5:35 p.m. yesteday, the tornado cut eastward through the city, across an interstate highway, and disappeared into the country. Reported to be a mile wide, the funnel destroyed thirty percent of the city, knocking out wired and cellular communications and forcing authorities to evacuate one of the town's two hospitals. The national guard has been deployed to the city.
Reuters' Mike Stone took these photos in the early hours after the disaster.

A member of the Neodesha fire department looks toward the St. John's Regional Medical Center a day after a tornado hit Joplin, Missouri May 23, 2011. The tornado blew the roof off St. John's where about 180 patients cowered and were eventually evacuated.

A sign lays among the ruins.

A stuffed animal is seen among the personal items scattered in the debris.

Ted Grabenauer sleeps on his front porch the morning after a tornado ripped off the roof of his home when it hit Joplin.

A view of the destruction after a tornado blew the roof off the St. John's Regional Medical Center.

A pool of blood is seen on the floor of a business establishment which was wiped out by the storm.

Scattered debris surrounds a damaged home.

Sheila Donham (R) and volunteers tend to an injured dog as they comb a neighborhood hard hit by the tornado.
Watch Iceland's Volcano Explode from Space [Volcanoes]
The world didn't break out in earthquakes but Grímsvötn, a volcano in Iceland, exploded over the weekend. The volcano sent a plume of ash and smoke nearly 8 miles high. Um, that's so huge you can see it from space. More »
iOS Devs Using In-App Purchases Urged to Play Nice
 The best course of action for iOS developers faced with patent infringement suit threats issued by patent holding firm Lodsys earlier this month might be to play nice with licensing requests, according to one intellectual property researcher. Florian Mueller, who runs the FOSS Patents blog that posted an in-depth FAQ for concerned developers last week, says that indicating a willingness to play nice with Lodsys could be far less costly than the alternative, in the long run.
The best course of action for iOS developers faced with patent infringement suit threats issued by patent holding firm Lodsys earlier this month might be to play nice with licensing requests, according to one intellectual property researcher. Florian Mueller, who runs the FOSS Patents blog that posted an in-depth FAQ for concerned developers last week, says that indicating a willingness to play nice with Lodsys could be far less costly than the alternative, in the long run.
Apple has yet to provide any official response as of this writing, and as Mueller points out, the 21 day consideration period Lodsys extended to developers is nearing its end, at least for those who received their notices first. It’s not guaranteed that Lodsys will begin legal proceedings once this grace period expires, but if the patent holder is serious about its claims, then a lawsuit is the next logical step. Mueller doesn’t want developers to agree to licensing deals sight unseen, he told me via email, but he does think the best course of action is threatened developers to get “Lodys to show [them] its proposed agreement, and to take it from there.” He argues though “chances are that Lodsys’s license agreement doesn’t contain anything particularly dangerous,” it’s still something that “must be reviewed by lawyers.”
Mueller argues that small developers could find themselves facing the very costly prospect of trying to mount a legal defense against a patent infringement claim, which, according to one lawyer speaking to MacWorld, could cost over $1 million in legal fees. Even if an initial defense is successful, Lodsys can and probably will appeal the decision and drag out the process by bringing it before higher and higher courts.
Developers risk confusing concrete legal threats with immediate, real-world consequences with moral and ethical considerations, Mueller warns. Devs may feel strongly that Lodsys is wrong, and that its behavior constitutes patent trolling, but that doesn’t mean you have the funds required to defend that belief. The harsh reality is that even if you end up paying Lodsys the full 0.575 percent cut it’s demanding from developers, you’ll still probably be far better off than had you chosen to mount a legal defense and taken this to court. Which, of course, is precisely the basis of the Lodsys business model: Threaten to sue and make the alternative much cheaper.
As for how developers can go about reaching a favorable agreement with Lodsys, if it comes to that, Mueller suggests that “developers share the cost of legal advice in connection with the proposed license agreement.” He says that more than a dozen of those targeted are already in contact and, that those devs should “share intelligence and [...] jointly analyze Lodsys’s proposed agreement,” but that ultimately, the costs associated with U.S. patent litigation are too high even for a combined effort mounted by small developers. Mueller sees no “alternative to a license deal unless Apple steps up to the plate,” he told me. Even the EFF made clear in its statement last week that while it disapproves of Lodsys’s actions, Apple is in the driver’s seat in this case.
In the long run, acquiescing to Lodsys’ demands means that developers are setting up the App Store model to die by a thousand cuts, since it means other patent holders can make similar claims on those using software tools provided by Apple and others as part of software development kits. But that’s a concern for Apple, Google and the other huge and powerful multinational companies that can afford to take a stand. Developers need to think about staying in business right now, and unfortunately, sometimes that means absorbing a few body blows so you can avoid the knockout punch.
Sony forecasts a $3.1B loss for FY 2011 due to quake, PSN failure
Sony has released a revised forecast for the now-finished fiscal year, noting that the company is expected to post a $3.1 billion loss, instead of the $857 million in profits forecasted back in February.
'Based on information currently available to Sony, our currently known costs associated with the unauthorized network access are estimated to be approximately ¥14 billion ($171.4 million) the fiscal year ending March 13, 2012,' Sony explained on a slide describing its losses. This does not include costs associated with lawsuits filed against the company, as the outcome of that litigation is hard to estimate for either side.
The company estimated a ¥17 billion ($208.1 million) loss of operating income this year due to the recent earthquake, and Sony also described 'incremental' losses, such as repair of structures and loss of inventory. 'The impact of these expenses is approximately ¥11 billion ($134.7 million); however, Sony has insurance policies which cover certain damages to fixed assets and inventories as well as the associated restoration costs, which are expected to offset almost all of these losses and expenses in the fiscal year ended March 31, 2011, as the recoveries from insurance claims are deemed probable.'
The natural disaster's impact of operating income for the fiscal year ending in 2012 is estimated to be a staggering ¥150 billion yen ($1.84 billion).
Sony admits that the situation could become worse if identify theft or credit card fraud is detected. 'So far, we have not received any confirmed reports of customer identity theft issues, nor confirmed any misuse of credit cards from the cyber-attack,' Sony stated, as reported by Joystiq. 'Those are key variables, and if that changes, the costs could change.'
Thursday, May 19, 2011
Verizon to Close the "All You Eat" Data Buffet, Offer “Family” Data Packages
Why Thunderbolt is Dead in the Water
US: if you hack us, we may use military action
 The US this week revealed its 'International Strategy for Cyberspace' with the subtitle of 'Prosperity, Security, and Openness in a Networked World' (via Ars Technica). The 30-page PDF document praises cyberspace and generally says nothing too exciting. It does, however, mention how the US government could respond to cyber-attacks, especially...
The US this week revealed its 'International Strategy for Cyberspace' with the subtitle of 'Prosperity, Security, and Openness in a Networked World' (via Ars Technica). The 30-page PDF document praises cyberspace and generally says nothing too exciting. It does, however, mention how the US government could respond to cyber-attacks, especially...

Apple to Customer Service: Don't Help Our Customers with Malware [Apple]
You'd like to think that customer service is out to serve the customers (you), right? Not exactly! After an unusually broad spread of Mac Defender, a piece of OS X malware, Apple is telling customers they're on their own. More »
Wednesday, May 18, 2011
Sony’s PlayStation Network password reset page compromised
According to reports from numerous gaming sites, the password reset page for Sony’s PlayStation Network has been exploited. Sony built the page in an effort to allow users, whose accounts were already compromised during a major security breach last month, to reset their security credentials. However, hackers who stole the information from Sony can reset users’ passwords by knowing and account holder’s email address and birthday — information they’ve already stolen. Forum members on Nyleveia have suggested that PSN users create a new email address specifically for use with PSN. Sony has taken the website offline, and said: “Unfortunately this also means that those who are still trying to change their password via PlayStation.com or Qriocity.com will still be unable to do so for the time being.” Sounds like Sony really needs to get those new security measures in place, stat.[Via Kotaku]
Microsoft replacing older 360s damaged by new firmware update
It seems that the latest Xbox 360 firmware update isn't compatible with all versions of the console, as a small number of users reportedly cannot play games on their systems after updating. To make up for this, Microsoft has confirmed that it will be replacing consoles for those affected.
'Following a recent update to our system software, we have become aware of an issue that is preventing a very small number of Xbox 360 owners from playing retail game discs,' a Microsoft representative told Eurogamer. 'This issue manifests itself a as a unique 'disc unreadable' or 'disc unsupported' error on the screen. We are also able to detect this issue over Xbox Live and are proactively reaching out to customers that may be impacted to replace their console.'
Those affected are urged to contact Microsoft in order to confirm that their consoles need replacement.
The new firmware is designed to support a new, updated disc format for the 360, which reportedly adds up to 1GB of usable data to Xbox discs. Microsoft will be replacing the outdated consoles with new 250GB slim 360s, and users will also be given one free year of Xbox Live to make up for the inconvenience.
Australian journalist arrested for reporting facebook security breach

Ben Grubb, a journalist in Australia, was arrested after writing a story about a security expert's demonstration of vulnerabilities on social media sites including Facebook. Two police officers showed up at his office, and interrogated him.
The officers were polite and there was even an amusing interlude when the female officer's iPhone rang, disrupting her recording of our conversations, and I gave Coultis some advice about how to set the iPhone to avoid further interruptions.
They seemed to treat me like a technical expert, and sought my explanation of what Heinrich had done. I felt like they were trying to get me to admit that his actions were illegal. I told them it was not my job to decide that - after all, I was only reporting on the matter. It's their job to decide whether what he demonstrated was against the law.
About half an hour into the questioning, Coultis left the room to liaise briefly with other officers. When he returned, he said: 'What we're going to have to do, I'm afraid, Ben, is we're going to be taking possession of your iPad.'
Rule number one, by the way, should this ever happen to you? Don't talk, other than to your lawyer.
Grubb's story: privacy, news and the strong arm of the law (Ben Grubb, in The Age)
Netflix now "the king" of North American Internet traffic

Metered billing and broadband caps be damned—consumer hunger for on-demand applications and video has put Netflix way out in front when it comes to data use. According to the Sandvine company's latest Global Internet Phenomena report, the online video company now accounts for 29.7 percent of all peak time wired network download traffic in North America.
Sony execs: We’re still investigating privacy breach, putting new security system in place
Speaking to The New York Times in an interview on Tuesday, Sony’s CEO Howard Stringer discussed the company’s recent security breach, and what his firm is doing to make sure such a large scale attack doesn’t happen again. Stringer argued that Sony reported the breach quickly, despite waiting nearly a week to notify its customers that hackers had stolen personal information, including credit card numbers. “We still have a lot of investigation to do to find out how this happened, but we’re not there yet,” Stringer explained. Sony’s corporate executive officer and executive vice president, Kazuo Hirai, said also noted that Sony is working to examine security on “every level of the company … from televisions to eBooks, and onwards.” Sony will create new security positions within the company, and the security employees with be tasked with setting up a “system to avoid this type of event again — putting a new system in place,” Hirai explained. Sony began restoring its PlayStation Network services in the United States last weekend after issuing a firmware update for the PlayStation 3.
Gigantic molecular windstorms can stop entire galaxies from forming new stars [Space Porn]
Molecular windstorms are ripping through the universe at 10,000 times the speed of the most powerful Earth hurricane. These super-sized storms can strip galaxies of the raw materials needed to make new stars in just 100 million years. More »
Tuesday, May 17, 2011
These Are the First Lego Sets Ever Launched Into Space [Space]
Yesterday, the space shuttle Endeavour launched for the last time, carrying the Alpha Magnetic Spectrometer and the ExPRESS Logistics to the ISS. But more importantly, it carried Lego to space for the first time in history. These are the sets. More »
Thursday, May 12, 2011
Transformers: The Complete Series
Visit Uncrate for the full post.
NASA's Dawn spacecraft captures first photograph of giant asteroid Vesta

NASA today released the first image obtained by the Dawn spacecraft of
the giant asteroid Vesta. The spacecraft should enter the protoplanet's orbit on July 16, when Vesta is about 117 million miles from Earth.
The image from Dawn's framing cameras was taken on May 3 when the
spacecraft began its approach and was approximately 752,000 miles
(1.21 million km) from Vesta. The asteroid appears as a small, bright
pearl against a background of stars. Vesta also is known as a
protoplanet, because it is a large body that almost formed into a
planet.
'After plying the seas of space for more than a billion miles, the
Dawn team finally spotted its target,' said Carol Raymond, Dawn's
deputy principal investigator at NASA's Jet Propulsion Laboratory
(JPL) in Pasadena, Calif. 'This first image hints of detailed
portraits to come from Dawn's upcoming visit.'
Vesta is 330 miles (530 km) in diameter and the second most massive
object in the asteroid belt. Ground- and space-based telescopes
obtained images of the bright orb for about two centuries, but with
little surface detail.
The processed image you see in this blog post was taken at a distance of about 1.2 million kilometers (750,000 miles).
Since Vesta is so bright that it outshines its starry background, Dawn team members commanded a long exposure time to make the stars visible. They corrected the resulting exaggerated size of Vesta by superimposing a short exposure image of the target asteroid, showing its true size.
More here about Dawn, and higher resolution versions of the image.
Tuesday, May 10, 2011
Mexican drug cartel builds its own tank [Video]
The war in northern Mexico between drug cartels and the Mexican government has raged for 4 1/2 years, with little end in sight — especially with the cartels starting to build tanks like this one, nicknamed "El Monstruo 2011.' More »
Monday, May 9, 2011
Apple surpasses Google as most valuable brand in the world
Apple has surpassed Google as world’s most valuable brand, according to advertising firm WPP’s “BrandZ Top 100 Most Valuable Global Brands” study. Apple’s brand value has ballooned 859% since 2006, and increased 84% to $153.3 billion this year. Tech companies dominate the rankings: AT&T, China Mobile, IBM, and Microsoft all have spots in the top-10 most valuable brands list, and McDonald’s is the only non-tech brand in the top-5. Google had reigned supreme for the past four years before being displaced by Apple, and Amazon surpassed Walmart to become the No. 1 retailer. Hit the jump for the full report from WPP.
Apple becomes world’s most valuable brand, says WPP’s BrandZ
9 May, 2011
Emerging markets account for 19 of the top 100 brands according to WPP company Millward Brown Optimor in its 2011 study of the Most Valuable Global Brands
NEW YORK – Registering a staggering 84 percent increase in value over the past year, Apple has emerged as the most valuable brand in the world, ending the four-year reign of Google at the top of the table in the sixth annual BrandZ Top 100 Most Valuable Global Brands study.
The Apple brand, as calculated by Millward Brown Optimor, a WPP company, has increased in value by 859 percent since 2006 and now stands at $153.3 billion. Other key findings in the study are that during the economic recovery of the last year, the combined value of all the brands in the top 100 has risen by 17 percent and is now worth $2.4 trillion. In terms of geography, according to the 2011 BrandZ study, 19 of the Top 100 brands now originate in “BRICs” markets, versus only two in 2006.“The importance of brand for global business success is becoming increasingly significant,” said David Roth at WPP. “In the last year, the global economy shifted from recovery to real growth, the combined value of all brands in the Top 100 ranking has risen by 64 percent since 2006 and is now worth $2.4 trillion. Strong brands, while not immune to the vicissitudes of the market, are more protected, prepared, resourceful and resilient.”
The BrandZ Top 100 Most Valuable Global Brands study, commissioned by WPP and conducted by Millward Brown Optimor, identifies and ranks the world’s most valuable 100 brands by their dollar value, an analysis based on financial data combined with consumer measures of brand equity.
The Most Valuable Global Brands 2011
Rank Brand Value in $ million Brand value change from 2010 1 Apple 153,285 + 84% 2 111,498 - 2% 3 IBM 100,849 + 17% 4 McDonald’s* 81,016 + 23% 5 Microsoft 78,243 +2 % 6 Coca-Cola 73,752 +8 % 7 at&t 69,916 - 8 Marlboro 67,522 +18 % 9 China Mobile 57,326 +9 % 10 GE 50,318 +12 % *The Brand Value of Coca-Cola includes Lites, Diets and Zero
“Our brand valuations are a powerful measure of an organization’s ability to create real and lasting value for shareholders.” said Eileen Campbell, CEO of brand research company Millward Brown. “By nurturing its brand and constantly innovating, Apple is able to command a high price premium and weather economic turbulence, providing a global business success story that other brands can learn from.”“Business leaders can embrace brand management as a critical competency for building long-term financial value,” she added. “Compared with an overall improvement of 13 percent in the world’s equity markets during 2010, the best brands grew their value 30 percent faster.
Other key findings highlighted in this year’s research report include:• One in five brands is from the BRICs: This year, 19 brands come from emerging markets compared to two in 2006 and 13 in 2010. The growing presence of brands from BRICs in this global ranking highlights the expanding purchasing power of people in these countries. While many of these brands are buoyed by the size of their local customer base, many more now have international ambition including Petrobras in Brazil (No. 61 in the ranking with a brand value of $13.4 billion); ICICI Bank in India (No. 53 and worth $14.9 billion) and China’s largest search engine Baidu. Now listed on the NASDAQ index, Baidu has a brand value of $22.5 billion and moves up 46 places in the ranking to number 29. Despite these successes, consumers in the BRIC regions continue to favor Western brands. Louis Vuitton, for example, (for which Brazil is its second-largest market) benefited from the new energy and confidence in the BRICs region. Its 23 percent growth in brand value to $24.3 billion has helped this luxury retailer achieve 26th place in the ranking, a three-spot increase from 2010.
• Heritage brands stay relevant in a technology age: Coca-Cola (No. 6), GE (No. 10), IBM (No. 3) and McDonald’s (No. 4), stand out in this study of global brand strength as brands that have survived for more than 50 years. Leadership, strategy and tactics aside, what all of these companies have in common is their use of brand to remain relevant to consumers and drive global business success.
• Technology and telecom brands dominate the ranking: Technology brands, which make up one-third of the Top 100 brands, continue to demonstrate their relevance in our daily lives. While Apple leads the ranking, it is followed in second place by Google, with a brand value of $111.5 billion, and IBM in third place with a brand value of $100.9 billion. Facebook makes its debut in the Top 100 ranking this year at No. 35 with the highest increase in brand value, 246 percent, making the brand worth $19.1 billion. Online retailer Amazon also edged past Walmart to become the No. 1 retail brand and 14th overall, with a 37 percent rise in brand value to $37.6 billion.
• Fast food, luxury and technology brands led brand value appreciation: Each of the 13 market sectors covered in this study grew in value over the last year. Fast food led the sector growth (22 percent) followed by luxury (19 percent) and technology (18 percent). The oil and gas sector experienced the slowest rate of growth (1 percent).
• Tech and convergence create brand interdependencies: Brands are ever more dependent on their use of technology to win consumers’ hearts and minds. The brand values of Burberry, Chanel, Louis Vuitton and Coca-Cola all benefited from their use of technology for example by harnessing social media and apps. At the same time, the dependencies demonstrated in the physical world between applications, devices and operating platforms are creating similar branded interdependencies. Brands that are aware of the risks can leverage these associations to drive value and growth.
• Toyota reclaims position as most valuable car brand demonstrating the power of strong brands to recover from the most fundamental challenges to product efficacy and reputation. Toyota’s brand, which is rated by consumers as “great value,” rose 11 percent to $24.1 billion.
The BrandZ Top 100 Most Valuable Global Brands study is the only valuation in the world that takes into account what people think about the brands they buy alongside rigorous analysis of financial data, market valuations, analyst reports and risk profiles. The research report, which is available online, includes a ranking and analysis of the Top 10 most valuable brands for key regions of the world and 13 market sectors. Download the complete BrandZ ranking, including regional and category breakdowns. The rankings and a great deal more are also available as a free application for the iPhone, iPad, Nokia, BlackBerry and Android from www.brandz.com/mobile
Friday, May 6, 2011
US Judge: an IP address is not a person
 In what could be a landmark decision, US Judge Harold Baker has ruled that an IP address is not adequate evidence to pin a crime on someone. For years, the recording industry has sued individuals for copyright infringement based solely on their IP address. This reached a new level when...
In what could be a landmark decision, US Judge Harold Baker has ruled that an IP address is not adequate evidence to pin a crime on someone. For years, the recording industry has sued individuals for copyright infringement based solely on their IP address. This reached a new level when...





 "
"





 "
"







 "
"


